SOPHOS UTM
Unified Threat Management and Endpoint Security
Your all in one network protection.

PRODUCT OVERVIEW
IT security products have become as complex as the networks they’re trying to secure. At Sophos, the solution to complexity is not more complexity. Sophos tackles security challenges with clarity and confidence, knowing that simple security is better security.
Sophos began producing antivirus and encryption products nearly 30 years ago. Today Sophos products help secure the networks used by 100 million people in 150 countries and 100,000 businesses.
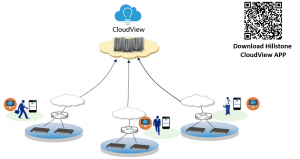
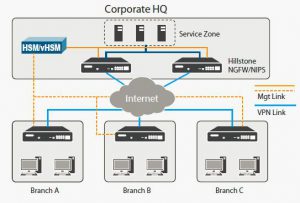
As IT networks grow in complexity, Sophos is focused on keeping IT security simple and reliable. Sophos knows that a proper security strategy must include networks, servers and devices—all devices—managed easily through the cloud.
Sophos products allow you to secure every end point of your network, from laptops to virtual desktops and servers, to web and email traffic and mobile devices. What’s more, securing these devices is made possible through products that fit your precise needs; to ensure your network’s security by providing the one thing no one else can: Simplicity.
Deep Learning Protection
Sophos UTM drives threat prevention to unmatched levels. The artificial intelligence built into Sophos Sandstorm is a deep learning neural network, an advanced form of machine learning, that detects both known and unknown malware without relying on signatures.
Lightning Speed
Sophos UTM is engineered to deliver outstanding performance. We built our UTM using Intel multi-core technology, solid-state drives, and accelerated in-memory content scanning. Potent, powerful … fast!
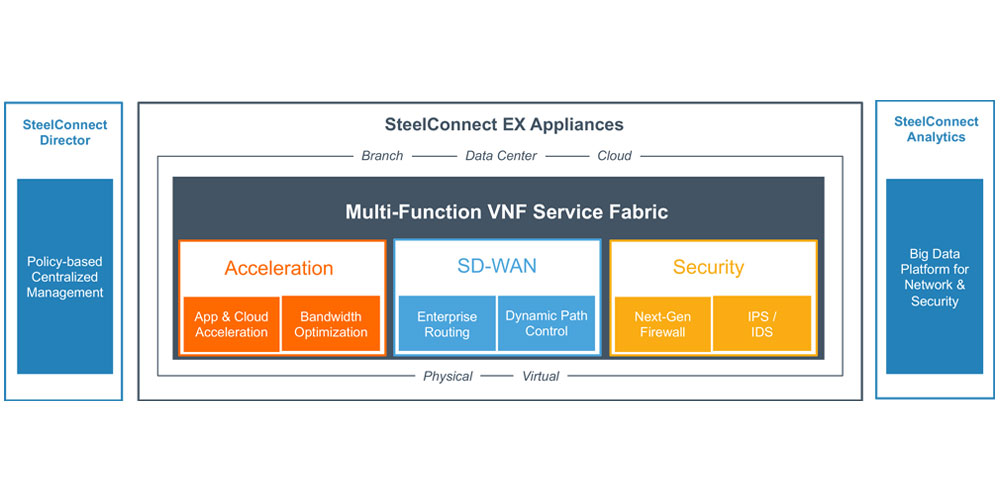
All-in-One Protection
We offer the latest next-gen firewall protection you need, plus features you can’t get anywhere else – including mobile, web, endpoint email encryption, and DLP. No extra hardware. No extra cost. Simply choose what you want to deploy.
Logging & Reporting
Sophos UTM built-in reporting means you’ll know exactly what’s happening with your users. Fix problems fast and shape your policies, keeping your users secure while boosting network performance. And, you get detailed reports as standard, stored locally with no separate tools required.
Miercom Test Results
As a Gartner Magic Quadrant Leader for UTM, Mobile Data Protection and Endpoint, we're at the forefront of the security industry.

Sophos UTM is easy to use thanks to the configurable real-time dashboard, flexible modular licensing, and intuitive reusable network object definitions.
Warning: Undefined array key 1 in D:\InetPub\vhosts\naizakdistribution.com\httpdocs\wp-content\plugins\jet-elements\includes\addons\jet-elements-video.php on line 2082
Warning: Undefined array key 1 in D:\InetPub\vhosts\naizakdistribution.com\httpdocs\wp-content\plugins\jet-elements\includes\addons\jet-elements-video.php on line 2082
Warning: Undefined array key 1 in D:\InetPub\vhosts\naizakdistribution.com\httpdocs\wp-content\plugins\jet-elements\includes\addons\jet-elements-video.php on line 2082
Warning: Undefined array key 1 in D:\InetPub\vhosts\naizakdistribution.com\httpdocs\wp-content\plugins\jet-elements\includes\addons\jet-elements-video.php on line 2082